There are a number of steps that organizations must take under NIS2 to ensure that their systems are adequately protected against cyberattack. These steps include adopting a formal cybersecurity risk-management policy that addresses the cyberattack risk and conducting regular risk assessments, access control training for employees, implementing security measures such as firewalls and encryption, and periodically reviewing system security. Entities should also consider using a secure automation platform, based on PLCnext controllers for instance, that is certified to the IEC 62443 series of standards. Such measures help ensure that entities’ networks comply with the EU’s NIS2 Directive and are adequately protected against cyberattack.
Rapid Transposition into National Law
NIS2 (Network and Information Security) is an EU directive designed to ensure that private and public operators of essential services have appropriate security tools to safeguard their systems against cyberattack. NIS2 is the successor to the NIS Directive, which entered into force in 2016. It provides for greater harmonization of cybersecurity measures in the EU states and central EU oversight, and extends the scope of the directive to include medium-sized entities that employ more than 50 employees and have an annual turnover and/or annual balance sheet total exceeding €10 million. The NIS2 Directive, which entered into force on 16 January 2023, must be transposed into national law in all EU Member States by 18 October 2024. It applies to essential and important entities in the EU.

NIS2 requires organizations to adopt appropriate technical and organizational measures to address the risk of cyberattack. An ‘essential entity’ can be broadly defined as “a service that is essential for the maintenance of critical societal or economic activities”. This includes organizations that provide essential services, such as energy (electricity and gas generation, storage, and supply), water (drinking water and wastewater), transport (rail, water, and road transportation), and digital infrastructure. Important entities are medium-sized and large entities whose services fall under the seven defined sectors, which are vital to the economy and society. Examples include organizations involved in the production and supply of food or chemicals, or the production of electrical equipment, machinery, and vehicles.
Threat Mitigation Measures
EU Member States are required to submit a list of the names of essential entities to the EU by 17 April 2025, which will be reviewed every two years. The entities named must comply with the requirements of Chapter IV of the NIS2 Directive, such as the Cybersecurity Risk-Management Measures set forth in Article 21 or the Reporting Obligations of Article 23. Cybersecurity risk management measures describe appropriate and proportionate technical, operational, and organizational measures that must be taken to manage the risks posed to the security of network and information systems in order to prevent or minimize the impact of incidents on recipients of their services and on other services.
These measures shall be based on an all-hazards approach that aims to protect network and information systems and the physical environment of those systems from incidents, and shall include at least the following:
- Policies on risk analysis and information system security
- Incident handling
- Business continuity, such as backup management and disaster recovery, and crisis management
- Supply chain security, including security-related aspects concerning the relationships between each entity and its direct suppliers or service providers
- Security in network and information systems acquisition, development, and maintenance, including vulnerability handling and disclosure
- Policies and procedures to assess the effectiveness of cybersecurity risk-management measures
- Basic cyber hygiene practices and cybersecurity training
- Policies and procedures regarding the use of cryptography and, where appropriate, encryption
- Human resources security, access control policies, and asset management
- The use of multi-factor authentication or continuous authentication solutions, secured voice, video, and text communications and secured emergency communication systems within the entity.
High Administrative Fines for Non-Compliance with Reporting Obligations and Requirements
The reporting obligations state when and how organizations must report significant security incidents to a national Computer Security Incident Response Team (CSIRT). Early warning is required after 24 hours at the latest, with an update to be provided on the severity and impact, as well as indicators of compromise, within 72 hours. A final report should be submitted not later than one month after the incident notification, providing a detailed description of the incident, including its severity and impact, the nature of the threat, and applied and ongoing mitigation measures. Recognizing that these requirements are challenging, the EU sets out appropriate supervisory or enforcement measures to be taken by the Member States (Articles 32/33), with administrative fines ranging from a maximum of at least EUR 7,000,000 or of a maximum of at least 1.4% of the total worldwide annual turnover in the preceding financial year, to EUR 10,000,000 or of a maximum of at least 2% of the total worldwide annual turnover in the preceding financial year, depending on the type of entity (Article 34). The management bodies of entities are responsible for implementing and overseeing the implementation of cybersecurity measures (Article 20).
To promote the convergent implementation of the required measures, it is important that Member States encourage the use of European and international standards and technical specifications relevant to the security of network and information systems (Article 25). These standards define secure products and principles for cybersecurity system design. One such standard is IEC 62443, the leading international series of standards defining requirements and processes for implementing and maintaining electronically secure industrial automation and control systems (IACS).
Certified Automation Platform for Comprehensive Security

PLCnext Control from Phoenix Contact is a non-proprietary automation platform certified to IEC 62443-4-1 ML3 and IEC 62443-4-2 and offers an extensive range of security level 2 (SL2) functions. Entities that use PLCnext Control benefit from comprehensive security functions that enable the secure operation of machines and systems. PLCnext Control’s security concept supports entities in both protection and incident response. Phoenix Contact also offers a 360-degree security strategy to ensure that its customers not only have access to secure products, but also to system design and consulting services backed by all relevant IEC 62443 certifications.
This paper provides an initial overview of the NIS2 Directive. Detailed information can be found in the directive itself and, where available, in the national laws of the EU Member States.
360-Degree Security Across All Processes
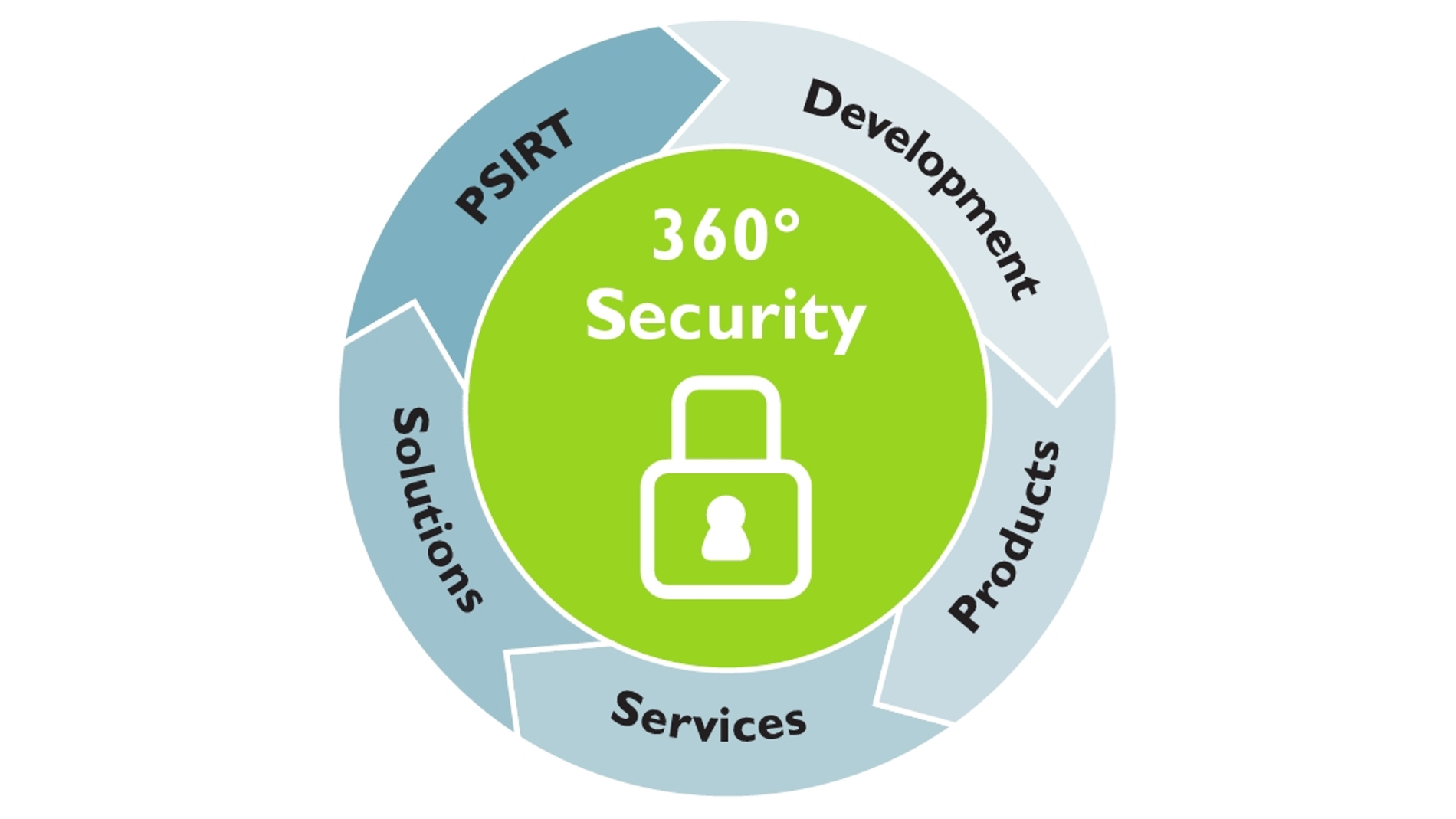
As systems and production become increasingly connected and digitalized, holistic security requirements are also rising. It is vital that people, machines, and data are protected to as great a degree as possible. The 360-degree strategy of Phoenix Contact includes both technical and organizational measures for comprehensive system protection. Phoenix Contact also offers secure services like consulting and training, develops secure solutions with zone concepts and data flow control, and anchors security in the entire life cycle of the products – from development through to regular updates. The final functional element of the 360-degree strategy is the PLCnext Control automation platform, which is certified to IEC 62443-4-1 ML3 and IEC 62443-4-2 SL2.
Reference: Dipl.-Ing. Boris Waldeck, Product and Solution Security Expert, Phoenix Contact Electronics GmbH, Bad Pyrmont
The previous content is supported by our partners.

